A Cybersecurity Defense to Help You Stay on Course

Defense in Depth – for a Long-term and Robust Cyberdefense
Imagine a cargo ship traveling on a stormy sea. On board is everything that is valuable to your business: systems, data and business-critical processes. On its journey, the ship is threatened by icebergs below the surface, sudden storms and attacks from unexpected directions. This is not a scene from a disaster movie. It is the digital reality that most connected businesses face every day.
In our new film, we show how it takes more than a strong hull or a skilled captain to get the cargo to its destination. It takes a strategy where no single defense is enough, but where strength lies in the whole. That’s exactly what we mean by Defense in Depth.
What Defense in Depth means
Defense in Depth is a well-established cybersecurity concept that is also defined by the US National Institute of Standards and Commerce (commonly abbreviated as NIST) as:
“An information security strategy integrating people, technology, and operations capabilities to establish variable barriers across multiple layers and missions of the organization.”
In other words, it is not about relying on a single technical solution or point effort, but building a safety net across the entire infrastructure of the organization: technical, organizational and human.
At the heart of the strategy are three intertwined dimensions:
- People: Employees' risk awareness, behavior, and ability to act correctly under pressure during incidents.
- Process: Structures, routines, and decision-making processes that ensure rapid and correct handling of incidents and risks.
- Technology: Systems and tools that protect, detect, and restore, automated and in real time where possible.
Defense in Depth is not just a technical framework, it is a strategy for organizational resilience.
The Capabilities Needed for Defense in Depth
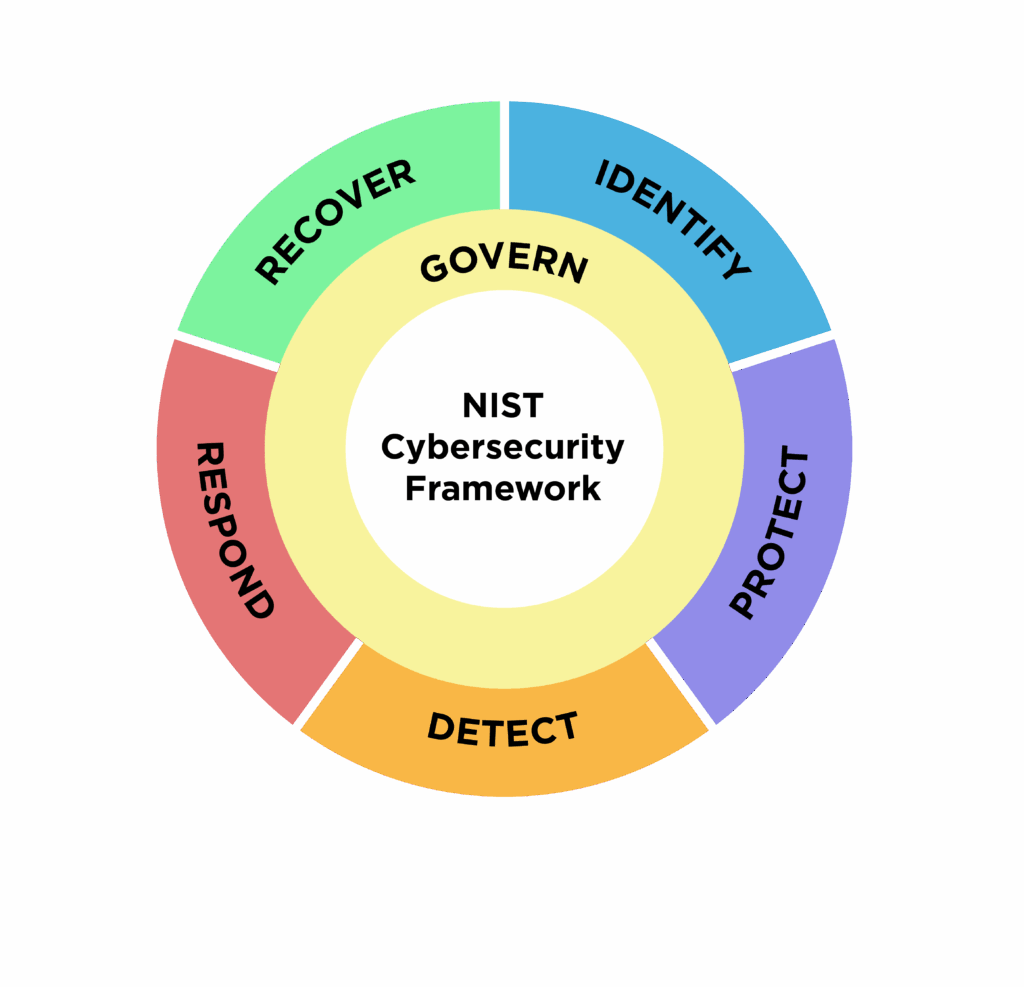
Building a cybersecurity defense that stays the course is about establishing capabilities that carry through the entire journey. According to the NIST Cybersecurity Framework 2.0, six core capabilities are required that together create long-term resilience. Read more about NIST’s Cybersecurity Framework here (PDF).
Again, imagine our digital journey as a ship at sea. To both navigate and survive the journey, we need the following:
- Governance. To steer the ship. Establishing direction, policies and responsibilities. Who is at the helm? Are the mandate, budget and governance in place?
- Identification. Understanding the cargo and risks. Map assets, data, vulnerabilities and threats – the foundation of all security.
- Protection. Building the hull. Protective measures that keep threats out: segmentation, authentication, training, firewalls.
- Detection. Having sensors in the hull. Detect anomalies and intrusions in time with logging, monitoring and SOC.
- Response. Acting when the alarm goes off. Incident management, roles and actions to reduce damage and stop spread.
- Recovery. Getting the ship back on course. Backup, recovery, learning and continued operation – fast and controlled.
These capabilities are not stand-alone, they build on each other and are reinforced by a Defense in Depth approach. When each layer of defense is linked to one or more of these capabilities, a whole is created that not only protects, but provides the ability to continue to deliver the load, even after a storm.
A methodology that matches both threat and regulations
In today’s regulated landscape, a well thought-out cybersecurity strategy also becomes a response to laws and requirements. For example:
- NIS2 with stricter requirements on risk management, business continuity, incident reporting and protection of critical infrastructure.
- DORA, which focuses on the digital resilience of the financial sector, including testing and third-party management.
- The AI Act and the Cyber Resilience Act, where the focus on security needs to be built into the development of new technologies.
The common starting point is that information security and technical security must interact and that compliance is a continuous process, not a one-off project. In addition, business management is responsible for risk and compliance policies.
Regulations can be perceived as burdensome, but properly managed, they become an opportunity to build in security and structure that creates business value with the goal of achieving stronger resilience.
Technology is the enabler
– not the goal!
Building a multi-layered defense requires technological tools, but above all, it requires interaction between different solutions. NetNordic partners with market-leading companies to provide the best security options for a distributed cyber defense, to make the security environment greater than the sum of their parts.
Firewalls
Firewalls are essential for protecting a company’s network from cyber threats. They monitor and control incoming and outgoing traffic based on security rules, helping to block unauthorized access, prevent data breaches, and ensure compliance with regulations. Firewalls provide a strong first line of defense—keeping your business, data, and customers safe. Your firewall supplier should provide:
- Best-of-breed endpoint protection with advanced prevention and XDR.
- Leading network security that extends from data center to cloud.
- Cloud security with integrated architecture for consistent security wherever you are.
- AI-driven and automated SOC functionality that ties the entire ecosystem together.
When these components work together, the result is not just technological protection, but an AI-enabled security platform for modern, dynamic distributed IT.
Segmentation
Segmentation is the foundation of Zero Trust, the ground-breaking concept of stopping breaches by building walls around all instances, making lateral movement more difficult – to prevent unauthorized access to other parts of the environment. It’s important to look at:
- Segmenting workloads whether they run on-prem, in the cloud or in container environments.
- The ability to effectively prevent lateral movement in the event of a breach.
- Transparency in how systems communicate internally and the ability to enforce policies accordingly without major infrastructure rearrangements.
Creating micro-segmentation that allows a breach to remain an isolated breach, and not the beginning of a system-wide crisis is an important step to effective cybersecurity.
Security Awareness
In a world where people are the targets, protection must start with each individual. Human-centric security can not just be a buzzword but a strategy. Make sure to establish:
- Email security with advanced prevention technologies.
- Targeted and risk-based awareness training – nano-learning is all well and good, but it requires targeted training for the individuals exposed to attacks, based on job roles and context.
- DLP solutions that protect not only against data leaks but also uncontrolled information loss linked to generative AI, cloud services and insider risks.
Creating a link between technology and behavior is key – a safety net where employees are continuously updated in cyber risk awareness.
How NetNordic can help
NetNordic is not just a technology provider, we are a system integrator that helps build a cohesive cybersecurity defense based on the needs, risks and maturity level of the business. We start from your journey, your burden, your reality.
We help you to:
- Map risks and assets.
- Choose the right technologies and make them work together.
- Ensure that processes, technologies and people work as a whole.
- Meet regulatory requirements in a way that also creates value for the business.
- Validate that the protections in place (or being built) work – that the environment is sufficiently hardened and robust.
Resilience is about moving forward, despite storms and obstacles. It requires a distributed approach – where each step, from strategic direction to recovery, rests in the same whole.
That’s why we also need a ‘what if mindset’, constantly testing our assumptions and challenging our capabilities. Are we up to the task, even when conditions change? This is the question we must live with – and build for.
Table of Contents
Content subjects category
Content type
Related content
Contact Us
Feel free to call us directly on our telephone number +47 67 247 365, send us an email salg@netnordic.no, or fill in the form and we will get back to you as soon as possible! Thanks!